Phishing is a method of stealing confidential information by sending fraudulent messages to a victim. It is one of the most prevalent scams in Bhutan.These messages can be sent via email, SMS, social media, instant messenger or phone call. They can look extremely sophisticated and convincing, replicating legitimate messages from reputable senders.
As well as featuring official-looking logos and disclaimers, phishing emails typically include a ‘call to action’ to trick us into giving out our most sensitive personal information, from passwords to bank details.
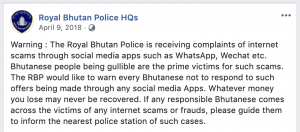
Various phishing scams have targeted customers of Bhutan Telecom, TashiCell and Bank of Bhutan(BoB). All citizens have a bank account that predominantly belongs to BoB and a phone number that belongs to either Bhutan Telecom or TashiCell, therefore it becomes easier for scammers to feature logos of such companies to lure people into clicking links and sharing personal information.All companies have been trying to sensitise the public about such scams through their social media handles as depicted below:
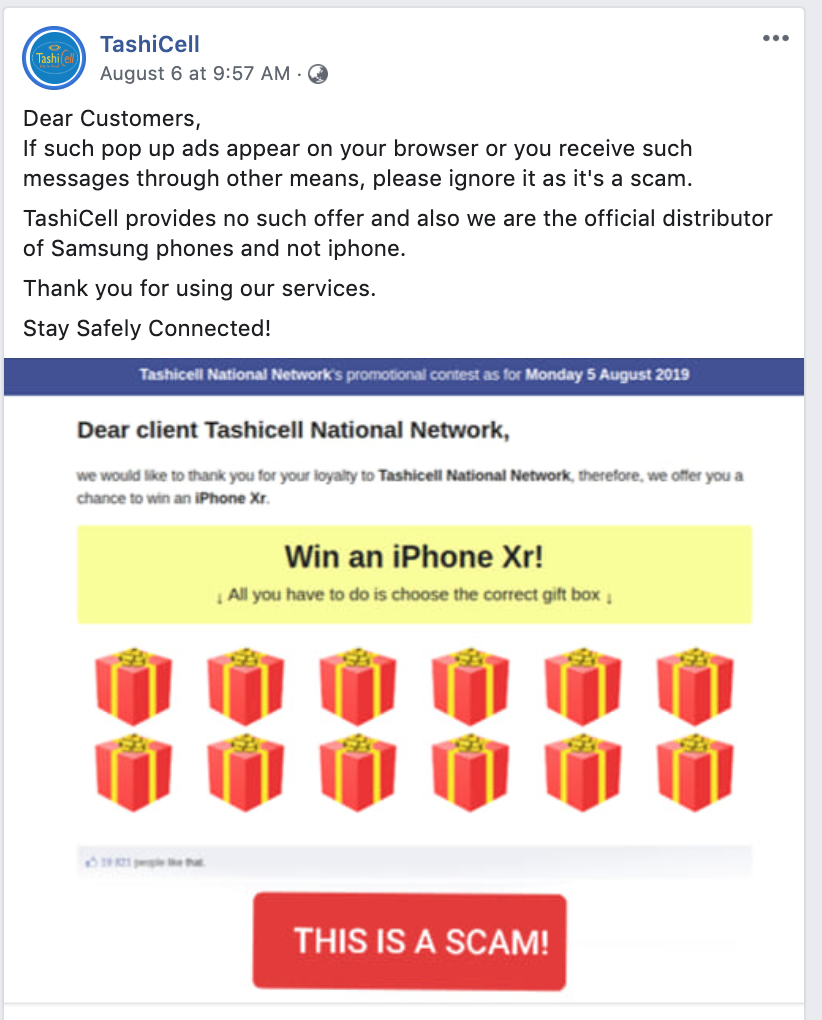
 Phishing cases in relation to Bhutan Telecom and TashiCell appears to be in the form of browser pop up ads(example on Facebook) such as the above and links shared through Whatsapp and Wechat.The cybercriminals or scammers offer eye-catching designs and statements to attract users attention, sometimes claiming you won an iPhone,a lottery or a Samsung phone and lure users in clicking links that subsequently ask for user credentials such as passwords and bank details or be asked to send certain amount of money to ship the products/lottery price money.
Phishing cases in relation to Bhutan Telecom and TashiCell appears to be in the form of browser pop up ads(example on Facebook) such as the above and links shared through Whatsapp and Wechat.The cybercriminals or scammers offer eye-catching designs and statements to attract users attention, sometimes claiming you won an iPhone,a lottery or a Samsung phone and lure users in clicking links that subsequently ask for user credentials such as passwords and bank details or be asked to send certain amount of money to ship the products/lottery price money.
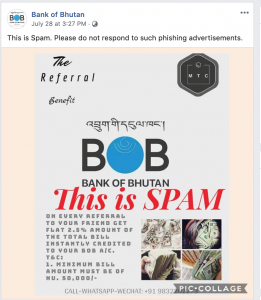
The BoB has also alerted their customers on similar phishing links and advertisements where phone numbers are provided for users to contact the scammers, as depicted below:
Similar tactics were also devised using logos of big Bhutanese banking and insurance companies such as Tashi Bank and Royal Insurance Corporation of Bhutan(RICB) to make users believe that it comes from a legitimate source, as depicted below:

How to identify a phishing attack
Here are a few more signs of a phishing attempt:
- The email makes an offer that sounds too good to be true. It might say you’ve won the lottery, an expensive prize, or some other over-the-top item.
- You recognize the sender, but it’s someone you don’t talk to. Even if the sender’s name is known to you, be suspicious if it’s someone you don’t normally communicate with, especially if the email’s content has nothing to do with your normal job responsibilities. Same goes if you’re cc’d in an email to people you don’t even know, or perhaps a group of colleagues from unrelated business units.
- The message sounds scary. Beware if the email has charged or alarmist language to create a sense of urgency, exhorting you to click and “act now” before your account is terminated. Remember, responsible organizations do not ask for personal details over the Internet.
- The message contains unexpected or unusual attachments. These attachments may contain malware, ransomware, or another online threat.
- The message contains links that look a little off. Even if your spider sense is not tingling about any of the above, don’t take any embedded hyperlinks at face value. Instead, hover your cursor over the link to see the actual URL. Be especially on the lookout for subtle misspellings in an otherwise familiar-looking website, because it indicates fakery. It’s always better to directly type in the URL yourself rather than clicking on the embedded link.
How do I protect myself against phishing?
- Remember that reputable businesses locally and overseas (such as BoB, TashiCell, Bhutan Telecom, BNB, RICB, Google, Apple, and Facebook) don’t call or email to verify or update your personal information.
- Don’t open e-mails from senders you are not familiar with.
- Don’t ever click on a link inside of an e-mail unless you know exactly where it is going.
- To layer that protection, if you get an e-mail from a source you are unsure of, navigate to the provided link manually by entering the legitimate website address into your browser.
- Lookout for the digital certificate of a website.
- If you are asked to provide sensitive information, check that the URL of the page starts with “HTTPS” instead of just “HTTP.” The “S” stands for “secure.”It’s not a guarantee that a site is legitimate, but most legitimate sites use HTTPS because it’s more secure. HTTP sites, even legitimate ones, are vulnerable to hackers.
- If you suspect an e-mail isn’t legitimate, take a name or some text from the message and put it into a search engine to see if any known phishing attacks exist using the same methods.
- Mouseover the link to see if it’s a legitimate link.
- Before opening an email, consider who is sending it to you and what they are asking you to do. If you’re unsure, call the organisation you suspect the suspicious message is from using contact details from a verified website or other trusted source.
- Use email, SMS or social media providers that offer spam and message scanning.
- Don’t provide personal information to unverified sources.
- Use two-factor authentication on all essential services such as email, bank and social media accounts
References:
- https://www.malwarebytes.com/phishing/
- https://www.phishing.org/what-is-phishing
- Facebook pages of BoB,RBP,TashiCell,Bhutan Telecom

