Ransomware is a type of malware that blocks access to computer system either by locking the systems screen or by encrypting files and folders usually demanding a ransom to unlock. For most of the new variants of ransomware, prevention has become the only guard since data recovery after attack is almost impossible.Though no huge harm has been done in Bhutan till date by Ransomware, personnel drives and PCs have been found infected and the trends elsewhere could soon be in. Statistics from Microsoft depicting Ransomware trends from December 2015 to May 2016 is as below:
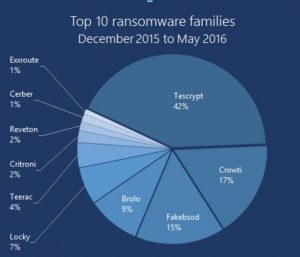
Most of the Security researches show noticeable
rise in Ransomware attack thus, BtCIRT urges all its constituencies to be aware of these growing trends and follow Mitigation measures.
Not being cautious enough would result in financial and reputational losses, disruption to regular operations and loss or leak of sensitive and critical information.
Affected Systems:
Currently Windows systems are primary targets but Mac, Linux, Android systems and even smart TVs are vulnerable. For instance, Mac Defender Malware is targeted to MAC OS.
Some Ransomware are also known to propagate to and encrypt data in whole of the shared network.
How it Works:
It spreads via compromised websites, spam email attachments,malicious advertisement, downloaded programs and Infected Removable drives.Spam emails are known to be most common platform used by attackers to send malicious attachment or links. The attacker sends emails with attachment which looks like from legitimate source for instance police or Tax enforcing agency and with threatening note like if you don’t pay within this time you will be penalized. Payment modes are usually in Bitcoins. When the victim opens the file the machine gets infected.
Some sort of warning message is displayed on screen once the machine has been compromised, for instance:
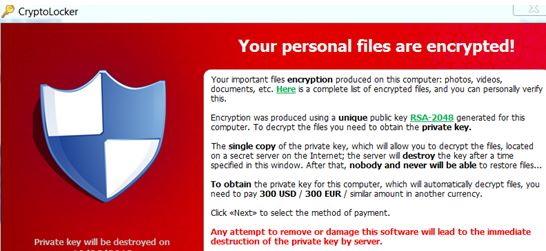
Mitigation:
- Back up: Periodically Keep online and offline backup of your data and verify their integrity.
- Keep your operating system and all other applications up-to-date
- Install and patch Anti-Virus Constantly
- Scan external drives and downloaded programs before running them.
- Be warned of what you are clicking on: A single click would lead to your system being compromised.
- Download programs and softwares from legitimate source.
- Restrict Administrator Privilege to Operating system and application based on user role.
- Make use of Multi-factor authentication wherever possible
- Use Strong Password and change them periodically, enabling “Remember password” in browsers is not recommended instead make use of Password manager.
- Use application whitelisting to restrict malicious softwares from running
- Maintain centralized and time synchronised logs of computer and network events.
- Enable Microsoft office Macros only when required
- Always Encrypt sensitive data on transit or even on storing.
- Make use of encryption while exchanging confidential information via email( eg. make use of PGP key)
- Enable volume shadow copy feature, many of the malwares cannot reach these files.
Recovery:
- Disconnect from internet.
- Since paying ransom doesn’t ensure your system will be restored, it is advised not to pay the ransom.
- Clean the affected drive and restore from backup.
- Change passwords
Reference:
https://www.microsoft.com/en-us/security/portal/mmpc/shared/ransomware.aspx#what
https://www.asd.gov.au/infosec/mitigationstrategies.html
https://www.cuny.edu/about/administration/offices/CIS/security/advisories/Ransomware-Advisory.pdf
https://www.fbi.gov/news/stories/2016/april/incidents-of-ransomware-on-the-rise/incidents-of-ransomware-on-the-rise
https://www.csa.gov.sg/singcert/news/advisories-alerts/ransomware
https://www.cert.gov.au/advisories/ransomware
https://www.asd.gov.au/infosec/mitigationstrategies.htm
https://www.pcworld.com/article/3083772/security/how-greed-could-destroy-the-ransomware-racket.html

